Automated Coding Standards Compliance for C/C++

All coding standards in one tool
With QA-MISRA there are no hidden extras, coding language variants, or compliance module add-ons. It provides a single solution to automatically check your C or C++ source code for compliance against the most common international software safety and security standards.
QA-MISRA automates compliance for:
MISRA C
2012 (inc. Amendments 1, 2 & 3) and 2023 – C coding Guidelines
AUTOSAR C++14
C++ for Adaptive Autosar
JSF AV C++
C++ standard for JSFF-35 aircraft program
CWE 4.13
Common Weakness Enumeration
MISRA C++
2008 and 2023 – C++ Coding Guidelines
HIS Metrics
Hersteller Initiative Software
CERT C/C++
2016 – C/C++ Coding Guidelines
ISO TS 17961
2013 – C Secure Coding Rules
Compliance Matrices
The following documents, together, provide full compliance matrices for all the coding standards and classify the degree of support provided by QA-MISRA for each rule
Why use a coding standard
– Cut the cost of coding standards compliance
All safety- critical software development standards highly recommend or mandate the use of static analysis tools to ensure compliance with safe and secure coding best practice. International functional safety coding standards such as MISRA and AUTOSAR, and security standards such as CERT and CWE, have become the de-facto coding standards. QA-MISRA automates the static analysis of C and C++ source code targeted for complying with all these coding standards in a single tool.
Certification of static analysis tools can be a heavy compliance cost burden. QA-MISRA has been independently certified by SGS-TÜV SAAR GmbH and provides a Tool Certification Kit with everything needed out-of-the-box, available free of charge. A Qualification Support Kit is also available.
– Detect software errors early
Through static analysis with QA-MISRA, dangerous structures, problems with security, maintenance and portability can easily be found as soon as source code components are written. The earlier software errors are identified and eliminated in the development process, the more your costs are reduced. QA-MISRA checks for over 900 potential software errors in source code.
– Reduce risk of software failure
Product recalls and jeopardy of brand and corporate reputations can far exceed the development cost of each application. Static analysis for coding standards compliance as soon as source code is written is the first stage of software verification to reduce risk of failure. Project over-runs can be mitigated by shifting verification effort to the earliest stage in the software development lifecycle. This reduces the risks of delays during later testing and complete system analysis stages because compliant components are easier and more predictable to integrate.
Fitness for purpose litigation against companies and individuals is now an increasing risk. Companies who fail to follow industry best practices, such as coding standards compliance, cannot use the “state of the art” legal defence against such litigation.
– Shorten time to market
Industry leaders recognise the need to ship faster without endangering quality. QA-MISRA provides two key time advantages for development managers:
› Not delaying static analysis until a full system is available, means standards compliant components are easier to unit test.
› Automated code reviews for coding standards compliance , trains developers to produce code with lower error rates.
– Fast static analysis of source code
QA-MISRA analyses extensive and complex software packages very quickly, regardless of the size of the codebase. By targeting the static analysis on the coding standards compliance rules, developers can apply QA-MISRA from individual components to full systems as code is developed. This analysis speed becomes especially valuable for teams deploying automated CI/CD pipelines, to verify compliance quality on every branch check-in.
– Zero False Positives & False Negatives
QA-MISRA produces zero false negatives and zero false positives on syntactic rules. When also coupled with the sound static analyser Astrée, also zero false negatives and very low false positives are produced on semantical rules.
Zero false negatives mean more confidence the analysis has not missed problems. Lower false positives mean less wasted effort on assessing and discarding as ‘false’ a reported rule violation (alarm).
Which rules in the standard to configure
Configurable rulesets
Drill-down selection and combinations of different standards to individual rules and checks for each project, provide flexible configuration for projects with mixed C & C++, autogenerated code or manually written code. All alarm messages and rulesets can be selected, interactively filtered and explored in the GUI, or stored in configuration files for command line batch execution.
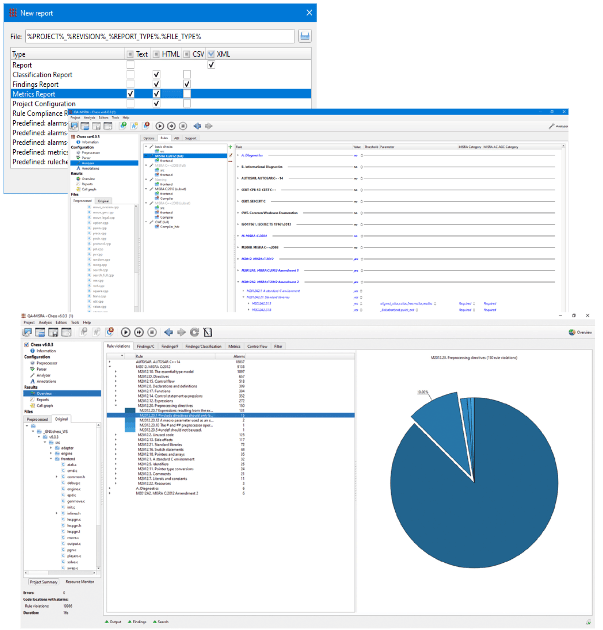
Offline detailed reports
QA-MISRA generates configurable reports in multiple open standard formats for offline compliance reports. This includes all alarm messages on source file level to be used in further automated processes or automatically distributed to offline users.
How to comply with the coding standards
Contextual rule explanations help developers understand and learn
For each rule violation detected, QA-MISRA details alarm explanations to reduce the effort to understand it’s root cause. All alarm messages refer to either original source file (Source phase checks) or a single occurrence in the source (even if the original code is included in multiple pre-processed files (Parsing and Analysis phase checks) – so identifying sole root cause.



